Free Software: When You’re the Product
Free software often isn’t free—you pay with your data. Learn how ad-supported apps monetize users, the risks involved, and how to choose privacy-respecting alternatives.

Free software often isn’t truly free—you pay with your personal data, attention, or behavior. Understanding this tradeoff is essential for protecting your privacy and digital rights online.
Free apps and services have reshaped how we communicate, work, and learn. But behind the convenience is a business model that frequently depends on extensive data collection, tracking, and profiling. This article explains what “you are the product” really means, how it affects your privacy and security, and what practical steps you can take to regain control.
Prefer listening? Click play below, or listen to this episode on RedCircle.
Powered by RedCircle
What does “free software—you are the product” actually mean?
When a service costs nothing to use, the company still needs revenue. In many cases, that revenue comes from collecting user data, analyzing behavior, and monetizing insights through advertising, partnerships, or resale.
This model has been well documented by privacy advocates and regulators because it often relies on behavioral tracking: companies and ad networks monitor what you do across websites and apps to build profiles that can be sold or used for targeted ads. The Electronic Frontier Foundation summarizes how this kind of cross-site tracking works and why it matters for privacy: Electronic Frontier Foundation
Free software isn’t automatically bad, but it often comes with hidden costs—reduced privacy, increased surveillance, and higher security risks if personal data is mishandled, breached, or repurposed.
How do free apps collect and monetize your data?
Most free services rely on a combination of technical and behavioral data collection methods. These can include account details, location data, device identifiers, browsing habits, and even inferred interests.
A major part of this ecosystem is the data broker industry, where companies collect, aggregate, and share detailed personal information about consumers without most people’s knowledge. The Federal Trade Commission’s report “Data Brokers: A Call for Transparency and Accountability” documents how data brokers amass and trade billions of consumer data points with limited transparency, often without consumers knowing who holds their data or how it’s used: Federal Trade Commission
Here’s how the pipeline typically works:
- Data collection – The app gathers information via permissions, tracking scripts, cookies, and third-party SDKs.
- Data sharing – Collected information is passed to advertisers, analytics platforms, or data aggregators.
- Aggregation – Data from many sources is combined into richer consumer profiles.
- Profiling – Detailed user profiles are generated for targeting or analysis.
- Monetization – Those profiles are sold, licensed, or used to optimize ads and engagement.
Because data brokers often operate behind the scenes and outside direct consumer interaction, users may have little awareness of how widely their information flows across the digital economy — and few practical tools to control it without intentional effort.
Protect your digital life—subscribe for trusted privacy and security insights.
Which popular free products show this model in practice?
Many well-known products rely on data-driven business models:
- Google services – Gmail and Google Search are free but funded largely through targeted advertising based on user activity.
https://www.google.com/policies/privacy/ - Facebook (Meta) – Social networking is monetized through detailed user profiling and ad targeting.
https://www.facebook.com/privacy/policy/ - TikTok – Short-form video is powered by intensive behavioral tracking to drive engagement and ad revenue.
https://www.tiktok.com/legal/privacy-policy
These companies offer real value, but their incentives are not aligned with minimizing data collection.
What are the privacy and security risks for users?
The risks extend beyond seeing more ads. Large-scale data collection increases the impact of breaches, enables government or corporate surveillance, and can expose sensitive information through inference.
According to the OECD’s work on digital security risk management, centralized data accumulation amplifies systemic risk when failures occur:
https://www.oecd.org/digital/security/digital-security-risk-management/
Key risks include identity theft, behavioral manipulation, discrimination through profiling, and loss of anonymity.
You can save this infographic for reference—it summarizes how free software monetizes users and where the privacy tradeoffs appear.
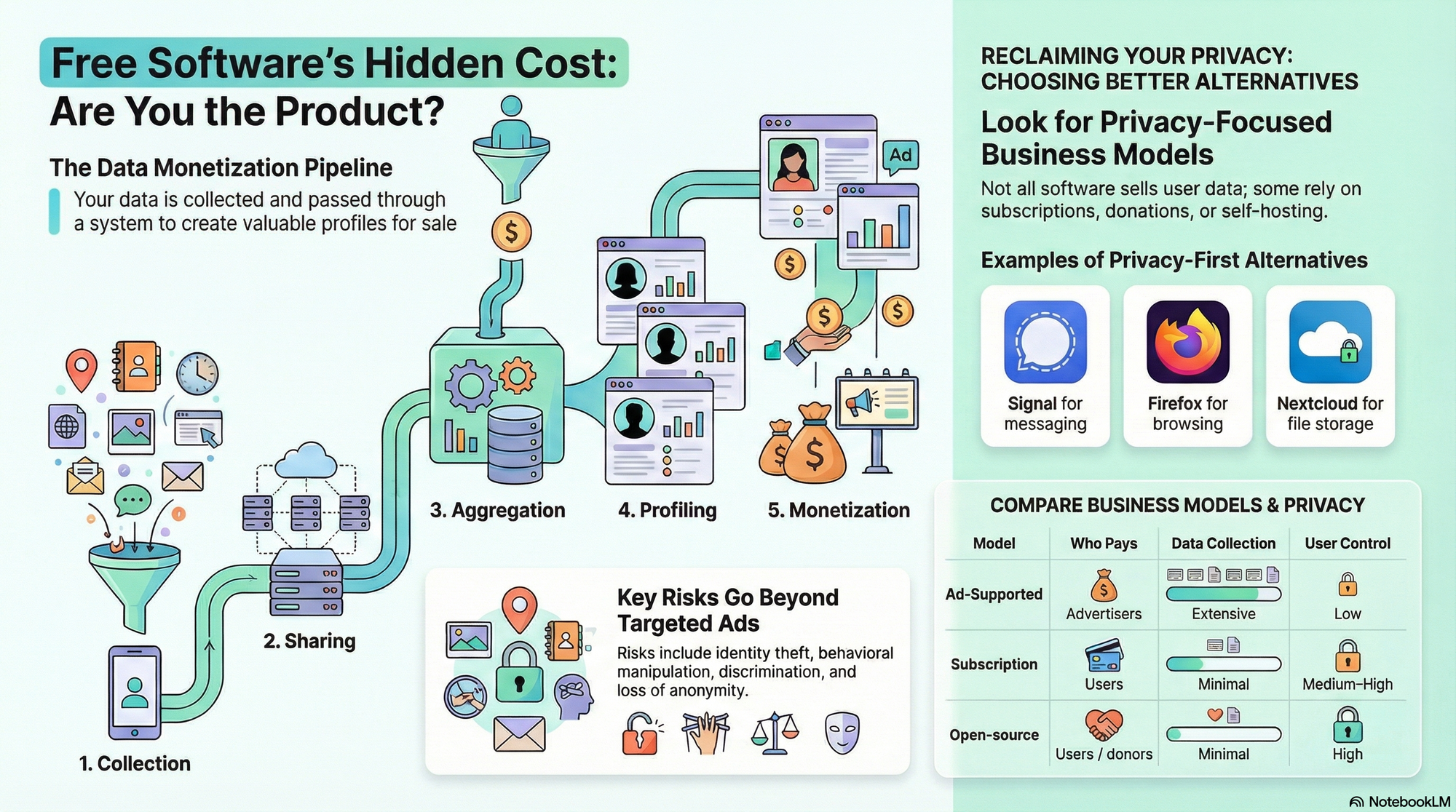
How can you choose privacy-respecting alternatives?
Not all free software treats users as products. Some projects use open-source development, donations, subscriptions, or self-hosting to align incentives with user rights.
Key differences at a glance
| Model | Who Pays | Data Collection | User Control |
|---|---|---|---|
| Ad-supported | Advertisers | Extensive | Low |
| Subscription | Users | Minimal | Medium–High |
| Open-source / self-hosted | Users / donors | Minimal | High |
Examples of privacy-first alternatives include:
- Signal for messaging (nonprofit, minimal metadata)
https://signal.org - Firefox for browsing (open-source, tracking protection)
https://www.mozilla.org/firefox/ - Nextcloud for file storage (self-hosted option)
https://nextcloud.com
Is free and privacy-friendly software possible?
Yes, but it requires sustainable funding models and informed users. Open-source communities, ethical subscriptions, and self-hosted tools demonstrate that software can be accessible without exploiting personal data.
The key is transparency: knowing how a product is funded, what data it collects, and whether you can opt out or take control.
FAQs
Is all free software bad for privacy?
No. The risk depends on the business model, not the price.
Why do companies want so much data?
Data enables targeted advertising, optimization, and long-term revenue growth.
Can paid software still track me?
Yes. Payment does not guarantee privacy—policies matter more than price.
What’s the safest option for sensitive data?
Open-source and self-hosted tools generally offer the highest control.
What to do next
Audit your most-used free apps today and replace at least one with a privacy-respecting alternative.


